The RIG Exploit Kit is currently at its most prolific, making up to 2,000 malicious attempts per day and succeeding nearly 30% of the time.
Exploiting vulnerabilities in Internet Explorer, the RIG Exploit Kit has been found to deliver a plethora of malware, including Dridex, SmokeLoader, and RaccoonStealer.
Prodaft recently published an in-depth report, gaining access to the service’s backend web panel, which revealed that exploitative kits remain a significant threat to the security of both individuals and organizations.
Eight years ago, in 2014, the RIG Exploit Kit debuted as an “exploit-as-a-service”, which allows other malicious actors to effectively exploit vulnerable systems and spread their virus.
Using malicious advertising, malicious actors inject malicious JavaScript scripts, known as RIG exploit kits, into exposed websites. Through this technique, they are able to spread their malicious intentions widely.
If a user accesses these sites, malicious scripts will be triggered that will attempt to use various browser vulnerabilities to quickly download malware onto the device.
In 2015, the creators of the kit released its second major edition, paving the way for more successful and extensive operations.
Unfortunately, in 2017, RIG suffered significant damage when an organized takedown operation destroyed much of its infrastructure and disrupted its operations.
After a brief hiatus, RIG re-emerged in 2019 with ransomware as its weapon of choice to wreak havoc on organizations. The malware helped Sodinokibi (REvil), Nemty and ERIS ransomware gain access to confidential data and capture their victims’ encryption keys for ransom.
In 2021, the owner of RIG stated that the service would be terminated – however, in 2022 they gave it new life with two exploits (CVE-2020-0674 and CVE-2021-26411 in Internet Explorer) that allowed them to achieve the highest success rate violations they have ever had.

In April 2022, Bitdefender notified the public that RIG was being used to install Redline malware to steal information from unsuspecting victims.
Although Microsoft Edge has succeeded Internet Explorer, millions of Enterprise devices still use the browser. This makes them a prime target for malicious RIG EK exploits.
Current attack volumes
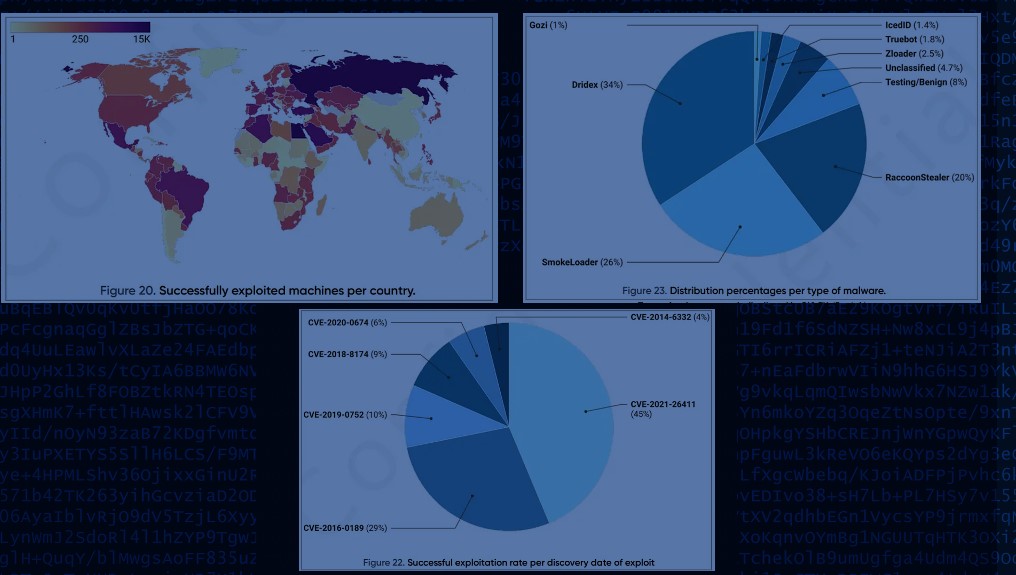
Prodaft reported that RIG EK is currently attacking 207 countries, with nearly 2,000 daily attacks and a 30% success rate. That figure was just 22% before the exploit kit made its reappearance, featuring two brand new exploits according to Prodaft.
As the report’s heatmap shows, Germany, Italy, France, Russia, Turkey, Saudi Arabia, Egypt, Algeria, Mexico and Brazil are among the countries most affected by this crisis. Nevertheless, it is a global issue with countless victims around the world.
Out of all the vulnerabilities, CVE-2021-26411 had a remarkable hit rate of 45%, while CVE-2016-0189 and CVE-2019-0752 got 29% and 10% respectively.
CVE-2021-26411 is a critical security risk for Internet Explorer users and was patched in March 2021. This memory corruption flaw is triggered by simply visiting a malicious website – so it’s important to be alert to potentially dangerous websites.
Internet Explorer is not exempt from the CVE-2016-0189 and CVE-2019-0752 vulnerabilities, which are capable of allowing remote code execution in the browser.
This February, CISA published an Active Exploit Notice for CVE-2019-0752 as a notification to system administrators that the vulnerability is still being exploited and should be patched with security updates.
A variety of malicious payloads
Currently, RIG EK mainly spreads data theft and raw access malware, with Dridex holding the largest share at 34%, followed by SmokeLoader (26%), RaccoonStealer (20%), Zloader (2.5% ), Truebot (1.8%) and IcedID(1.4%).
As expected, the malware spread through RIG EK is constantly changing as different cybercriminals use the service.
Prodaft detected the presence of multiple sophisticated ransomware, including notorious names such as Redline, RecordBreaker, Gozi and PureCrypter. Additionally, it has detected Royal Ransomware and UrSnif in their distribution process.
The distribution of the Dridex banking trojan is particularly interesting because there are indications that RIG operators have taken steps to ensure that its distribution goes smoothly.
We should not overlook the fact that the Entropy ransomware incidents were linked to Dridex a year ago, so the RIG EK hacks could be linked to data encryption incidents.
RIG EK poses a huge risk to users of outdated software, as it is known for its ability to sneak into systems and steal highly confidential information.
Despite RIG EK’s devotion to Internet Explorer, its future looks bleak as Microsoft discontinued IE in February 2023 and sent its customers to Microsoft Edge.



0 Comments